Summary
Introduction
This document summarizes the data being stored by Cryptolens AB (“Cryptolens”) to provide the service Cryptolens (https://app.cryptolens.io) and the protection measures we have in place to safeguard against accidental loss and data breach. It should be used for informational purposes only. If you are unsure, please consult a lawyer.Your rights and the rights of your customers
Depending on applicable data protection laws (such as the GDPR), you and your customers may have rights such as access, rectification, deletion, restriction of processing, data portability, and objection to certain types of processing. As a data processor, Cryptolens provides features and support to help you fulfil these obligations towards your end-users (for example, deleting or exporting license data). For the full description of these rights and how they apply, please refer to your own privacy policy and the data processing agreement you have in place with us.How to be compliant as a software vendor
Once you start distributing your software, you will most likely have users using it. Depending on if you sell to end users directly (eg. for desktop apps) or indirectly (eg. for SDKs), different steps have to be taken to ensure compliance. These different cases are summarized below: on the left is the when the end users are your direct customers and on the right is when the end users are customers of your customers.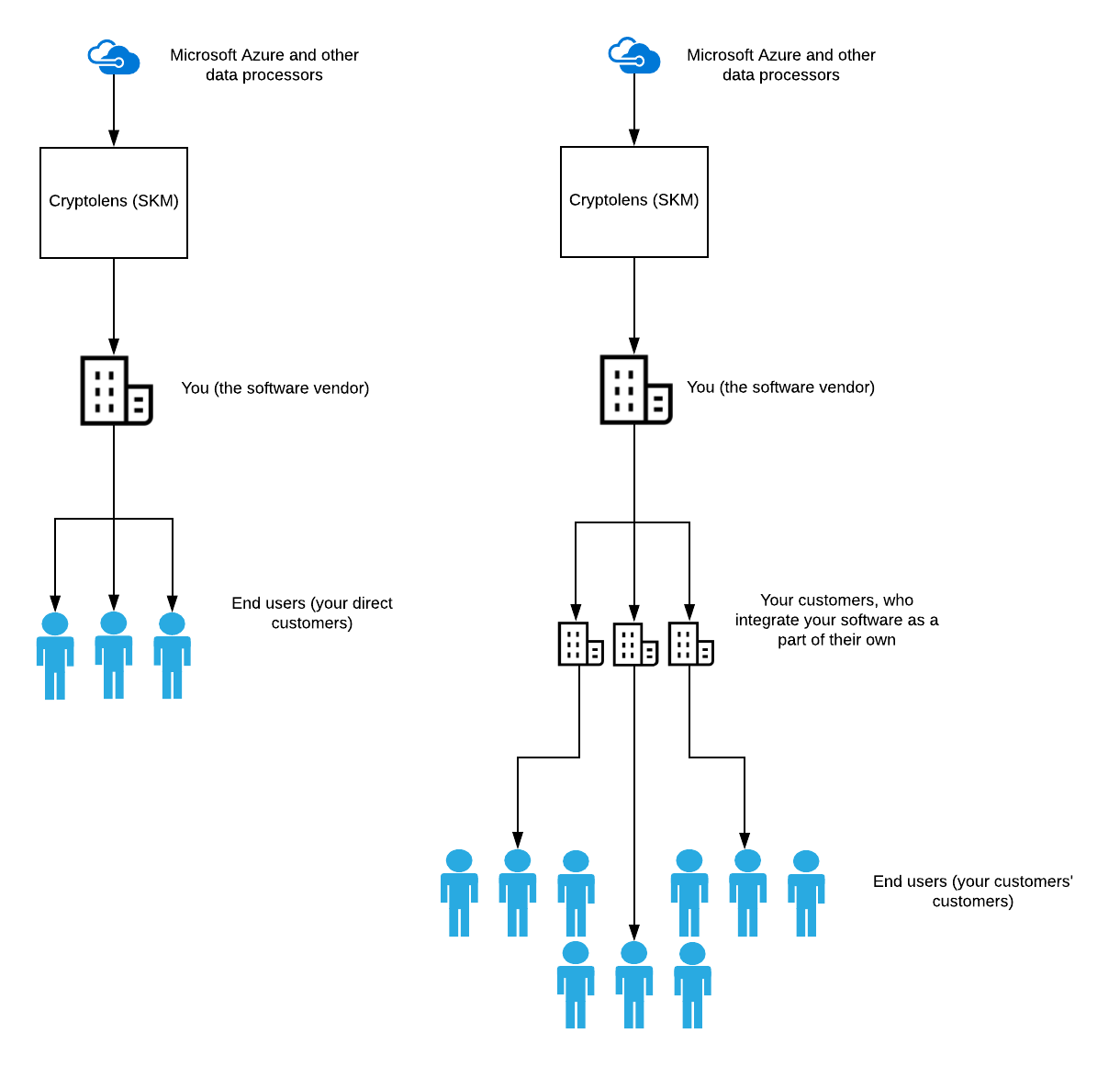
Compliance by default (update)
If you use Cryptolens as it is intended to be used, there is no need to include a consent in your agreement. The only personal data that Cryptolens needs is the IP address and Machine Code of the end user device. Both of these are needed to provide your customers the service.- IP address is needed to be able to spot unauthorized use of your software.
- Machine code is needed to be able to enforce your licensing model (eg. restrict usage of a license to a specific number of machines).
If you want to use this information for any other purpose, you need to obtain a consent from your customers.
What data we collect
In short, we collect two types of data: data about you and data about your customers. In cases where your customers integrate your software (eg. a library/SDK) as a part of theirs, the end user is also their customers. To make this as general as possible, we will go through the features in Cryptolens and describe who this data belongs to.Products
Products is a way of grouping licenses. Many of the parameters in a product such asname, description and licenses belong to you directly. However, if you collect information in the notes field or data objects that can be linked, directly or indirectly to a person, this then becomes personally identifiable information.
Note, be very careful with the way you define personal data, since even IP address are considered personal identifiable information. Even primary keys in a table can be considered as such, if they can be used to link the data, directly or indirectly, to a person.
Activated machines
In order to to be able to tell the difference between the computers/devices (we refer to them as machines) that have activated their license, we store an additional set of fields for each of those machines. This includes:Machine Code- a device identifierIP- the IP of the client device that performed the activation.IP Proxy- the IP of the proxy (Cryptolens backed) used to perform the activation.Time- the time of the first activation.FriendlyName- a identifier that you can pass to add a label to the device. It is used to help you and your clients to map a device to a certain user easier.
machine code and the IP address constitute personal identifiable information. We also have a record that links this to a certain key, but this is never returned through the API.
Logging
Activated machines are can be thought of as up-to-date records of who is entitled to use a license. Once they stop using the service (eg. by deactivating), this record will be removed. However, for statistical purposes, it can be useful to have a history of all licensing activity related activity:Pid- the product idKey- the key id of the key always returnedIP- the IP address that called this method. this is the client user’s IP. The anonymized IP address is used with the last bits masked.Time- the date and time when the activation was performed (the first time).Machine Code- a device identifierState- a number with a certain pattern that describes the request and its results.FriendlyName- a identifier that you can pass to add a label to the device. It is used to help you and your clients to map a device to a certain user easier.FloatingExpires- the time when the floating license should expire.DOIntValue- the int value associated with the data object.DOId- the id the data object that was involved in the request.
machine code and the IP address constitute personal identifiable information. In addition, we store your user id in order to ensure that we only return your records.
Customer objects
To facilitate grouping of licenses that belong to the same customer, we use the notion of customers. A customer object contains the following:Name- the name of the customer.Email- the email of the customer.CompanyName- the company name of the company the customer belongs to.
Account information
To make sure that we can send you correct invoice, we store billing information such as the company name, address, VAT Id. For security purposes, we store the history of IP addresses used to login on your account.Third party services
Please refer to the DPA for more information.History
- 2021.03.03 Update the data that is collected.
- 2020.12.29 Update the provider for transactional mail + add new security features.
- 2020.04.05 Update the list of third party services. Update the name of the service from SKM to Cryptolens.
- 2018.05.24 Update the consent requirement (i.e. you no longer need a consent from your customers to be compliant).
- 2018.03.16 First version.
References
- https://ec.europa.eu/info/law/law-topic/data-protection/reform/rights-citizens/my-rights/what-are-my-rights_en, Last accessed 2018-02-28.
- https://app.cryptolens.io/docs/api/v3/model/ActivationData, Last accessed 2018-03-06.
- https://app.cryptolens.io/docs/api/v2/WebAPILog, Last accessed 2018-03-06.
- https://app.cryptolens.io/docs/api/v3/AddCustomer, Last accessed 2018-03-06.
- https://app.cryptolens.io/docs/api/v3/Activate, Last accessed 2018-03-12
- https://app.cryptolens.io/docs/api/v3/GetKey, Last accessed 2018-03-12